Hack Prevention
How to Stop Brute Force Attacks on WordPress: 7 Plugins
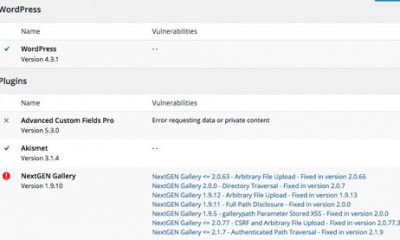
Keeping your WordPress site secure is an ongoing process. It is well worth taking on considering that WordPress sites get attacked by hackers all the time. You should not wait for brute force attacks to get coverage on popular blogs before making your site and server secure. We have already covered some of the basic steps you need to take to harden WordPress (e.g. change default admin name, lock admin pages by IP, …). Here are 7 plugins you can use to combat Brute Force attacks:
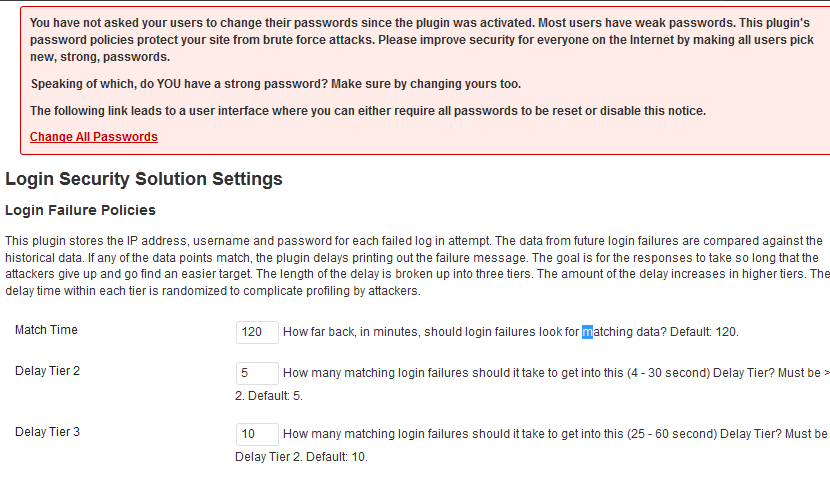
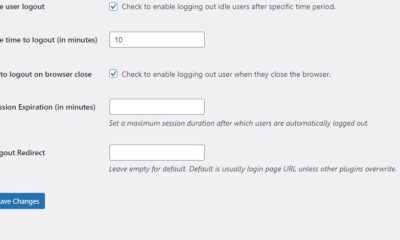
Login Security Solution: enables you to combat brute force and dictionary attacks more effectively. It tracks IP addresses, usernames, and passwords and logs out users when their account is breached.
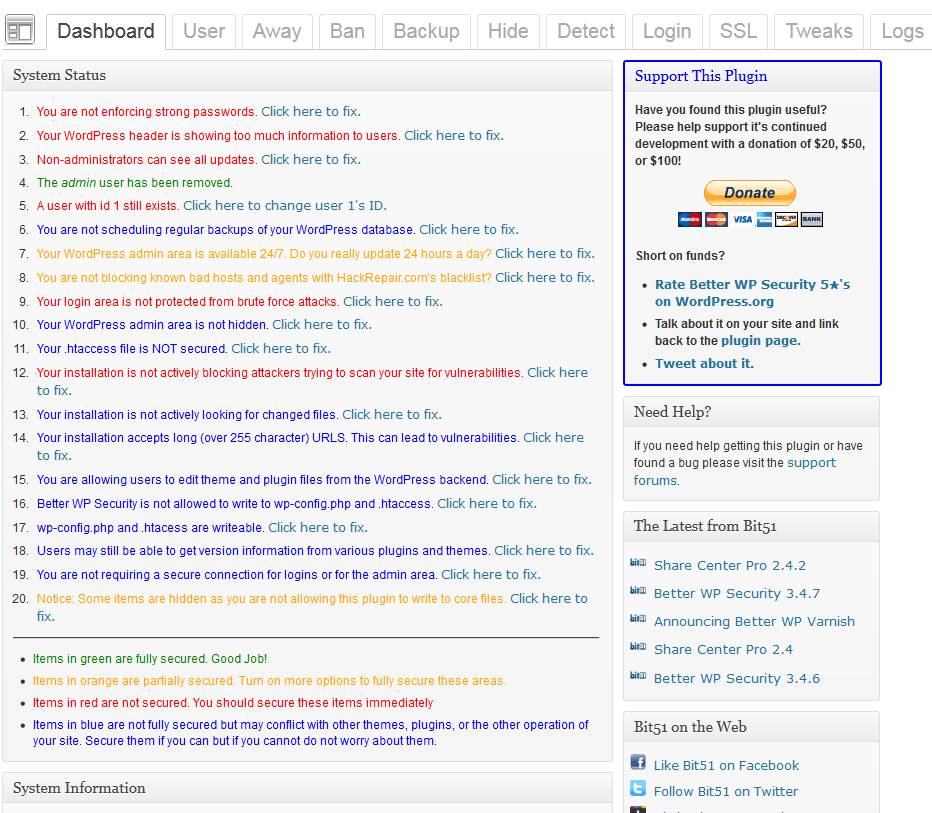
Better WP Security: one of the best WordPress security plugins around. It shows you what you need to be doing to secure your site. It helps you recover from hack attacks too.
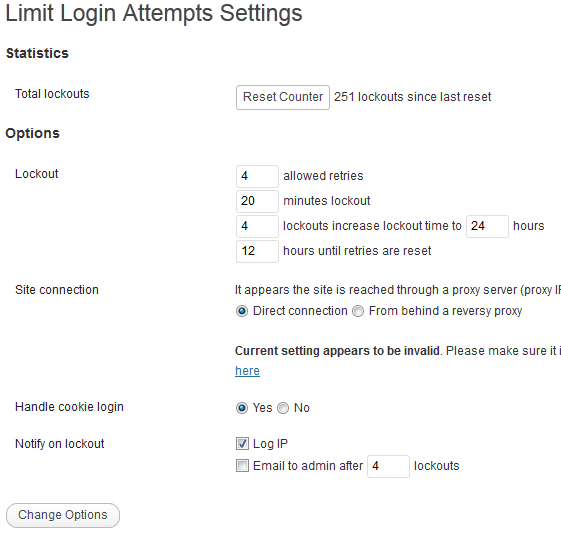
Limit Login Attempts: a simple tool that tracks failed login attempts and blocks attackers. It may not work against highly sophisticated attacks but does keep hackers from reaching your admin pages. Best of all, it alerts you when someone is messing with your login page.
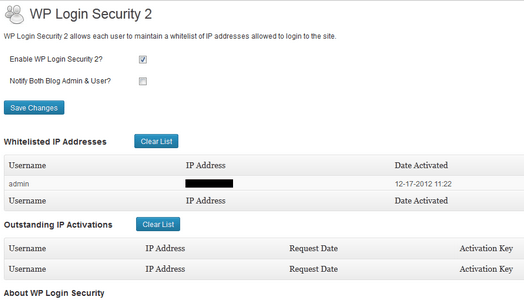
WP Login Security 2: this plugin requires users to whitelist their IP address. It keeps admins in the loop.
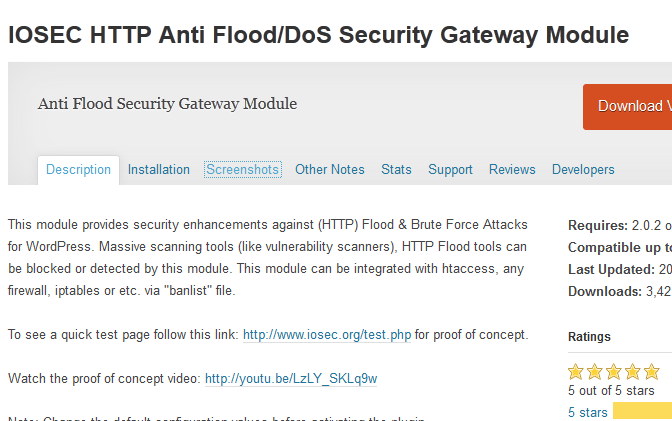
OSEC HTTP Anti Flood/DoS Security Gateway Module: one of many plugins you can use to combat DDoS and Brute Force attacks. It can be integrated with .htaccess.
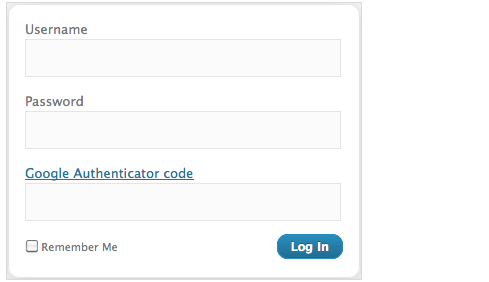
Google Authenticator: a simple tool that adds two-factor authentication to WordPress. This option can be enabled on a per-user basis.
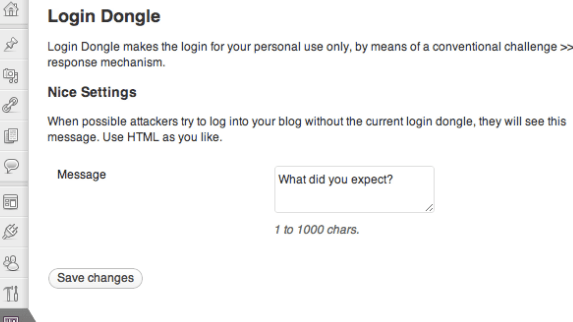
Login Dongle: allows you to log on to your site in a secure fashion. It adds an extra layer of security to your login page.
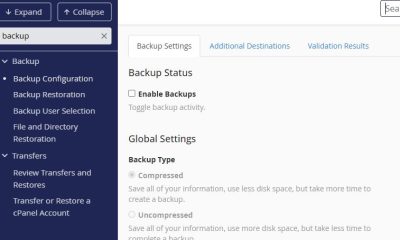
Installing CSF & CXS, restricting access to your login and admin pages by IP, and using security solutions such as Mod_Evasive could all help you make your serve more secure. WordPress security is not a process you should take lightly. Don’t forget to backup your sites regularly to be prepared for the worst case scenario.



Will
April 16 at 3:42 pm
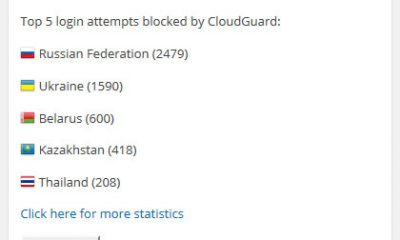
With the botnet launching these attacks from over 90,000 different IP addresses, wouldn't most of these login failure lockout tactics be useless? As Matt M said, they could just hit you with a different IP address every second for a day http://ma.tt/2013/04/passwords-and-brute-force/
Cyrus
April 16 at 3:51 pm
@Will. I wouldn't say useless. Matt is correct. Not all hack attacks are the same. That is not to say that CSF, CXS, Mod_Evasive, and Better WP Security are going to be useless. That is simplifying a complex problem. Also, we have covered limiting access by IP when using Nginx and Apache. I do agree with you that you can’t just use a couple of simple plugins to harden WordPress, which is why we have over a dozen of lists and tips articles on WP Security 🙂